The vast majority of exchanges now use encryption to guarantee the confidentiality and integrity of exchanges : HTTPS, SMTPS, LDAPS and many others. SSL (Secure Socket Layer) encryption, and its modern version TLS (Transport Layer Security) encryption are the most commonly encountered.
Although HTTPS is easy to set up, default or aging configurations are often vulnerable and do not guarantee the best level of security for the user. In addition, a bad configuration also leads to a reduction in the ratings assigned by cybersecurity products on which cyber insurance can be based.
How to test your TLS/SSL security?
In order to test the security of HTTPS encryption yourself, there are a few online solutions that allow you to easily measure it:
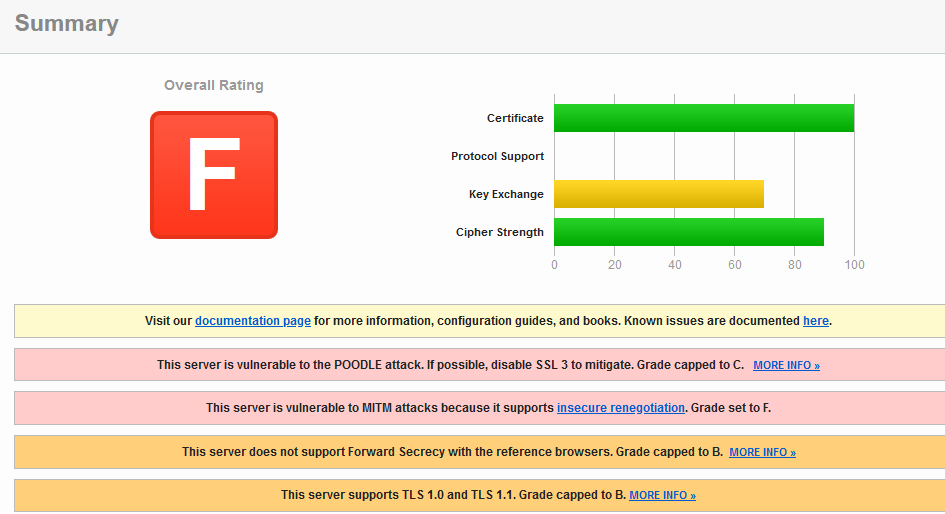
A score is then assigned to you, along with the details of the weaknesses.
Attention, by default the results are made public, remember to check the box “Do not show the results on the boards” or “Don’t include my site in the public results” respectively.
A more confidential alternative is to perform the analysis yourself using the testssltool (https://github.com/drwetter/testssl.sh).
For example on Kali Linux, type the following commands to analyze your website:
sudo apt install testssl.sh
testssl https://yourdomain/
The tool colors positive results in green and weak configuration in orange/red.
Understanding the results
The most common SSL/TLS vulnerabilities are:
- Use of outdated or vulnerable protocols (SSLv2, SSLv3, TLS 1, TLS 1.1)
- The use of weak algorithms (RC4, obsolete CBC ciphers on AES, ARIA etc.)
- Vulnerabilities in SSL/TLS implementation(Heartbleed, Ticketbleed, TLSStorm for instance)
In general, these vulnerabilities can allow a malicious actor in a Man-in-The-Middle position to decrypt communications if the conditions are met, or to attack web servers directly as in the case of Heartbleed (CVE-2014-0160) or Ticketbleed (CVE-2016-9244).
How to improve SSL/TLS security?
When you own the configuration of web servers, securing TLS encryption can be easily achieved by using the parameters recommended by Mozilla on the following online generator: https://ssl-config.mozilla.org/.
To use it, simply choose your type of web server or reverse proxy (Apache, IIS, Nginx, Traefik, others), as well as the desired TLS hardening level. The latter will also depend on the level of compatibility with old browsers (old PCs or smartphones).
It is generally recommended to use the “Intermediate” setting for a compromise between security and backwards compatibility, or “modern” for optimal security and score.
🛡️ DSecBypass supports you in securing your TLS services during website security audits or external penetration tests, with quality services and significant experience in this type of service. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
