This article aims to share the results of our experience of penetration tests carried out on websites built with WebDev and the HFSQL database. It is written for pentesters and security researchers who wish to study the security of these technologies, but also for curious developers.
It is important to emphasize that WebDev allows you to create secure web applications, but like all frameworks, it gives developers enough flexibility to introduce vulnerabilities.
We will see in particular the possibilities offered by HFSQL in the event of SQL injections, how to authenticate on an accessible HFSQL service, as well as the replication of a local WebDev environment to study its security.
Note: the illustration image was made with an AI, it is a comical reference to PC SOFT visuals which generally contain people who are not in cold countries.
WinDev, WebDev, HFSQL, WLangage
Before getting to the heart of the matter, a few definitions are in order.
First, WebDev != WebDav, isn’t it Nolan 🙂
WinDev: WinDev is a software engineering workshop (AGL) published by the company PC SOFT, the first version was created in 1993. This software allows you to design and develop applications in all areas. WinDev uses its own programming language, WLanguage, a simple, powerful language that is very quick to learn.
WebDev: WebDev is a web application development environment. It includes a code editor, visual design interface, pre-built components, and a built-in database. In addition, it offers easy deployment features to make web applications quickly accessible online. WebDev is popular, especially in France, with developers looking to create complex and powerful web applications, while benefiting from an intuitive user interface and rapid development features.
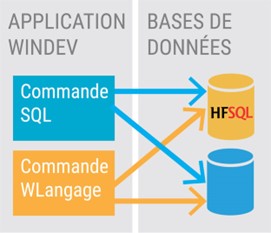
HFSQL: HFSQL (HyperFileSQL) is positioned as a relational database management system, offering advanced features for storing, organizing and retrieving data in a structured manner. In addition, HFSQL offers the possibility of using WLanguage, which offers advanced, easy-to-use and powerful functions, which reinforces its versatility and development capabilities. These two components, although distinct, can collaborate synergistically in the development of robust and secure applications.
Pentest of a WebDev application
Penetration tests on a WebDev and HFSQL web application are no different from those carried out on more widespread technologies: the vulnerabilities of the OWASP TOP10 can be encountered and the methodology remains that of a classic web pentest.
The application is most generally deployed on a Windows environment with an IIS web server, so adapt your wordlists in case of path traversal!
This article deals with two specificities which are not covered by the current tools available to pentesters: the exploitation of an HFSQL injection and authentication on the HFSQL service (most often on the tcp/4900 port).
Authenticate on HFSQL
It is common for the HFSQL DBMS port to be open on the Internet: WinDev thick clients may require access to this data or the database is hosted in an infrastructure different from the WebDev application. In any case, it is a dangerous practice: it is recommended to never leave the database service open on the Internet and to restrict its access (by whitelisting IP addresses, by VPN, or others).
There are no easy-to-use tools to test the validity of an account on an open HFSQL service. Indeed, this requires the use of a specific ODBC driver, which is difficult to integrate into tools like Metasploit or Hydra (from a technological but also legal point of view).
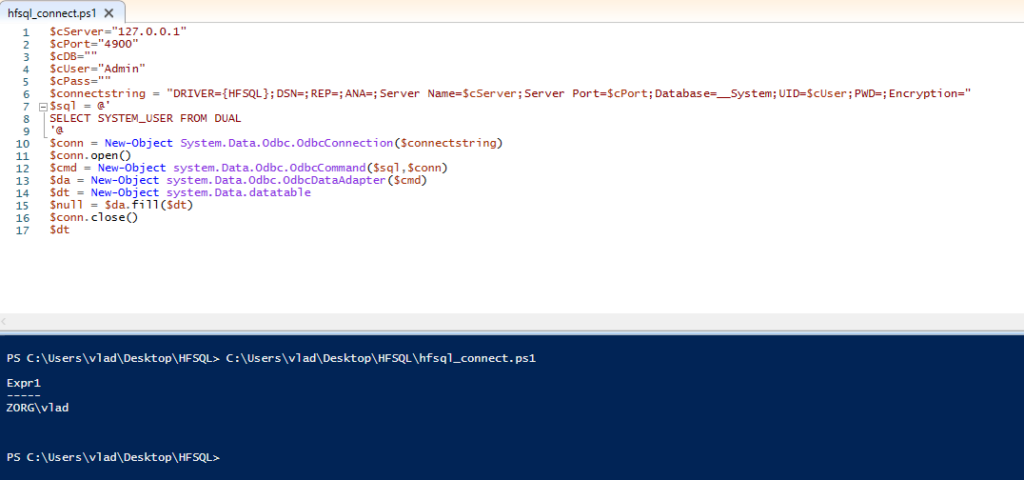
The solution proposed here is the use of a Windows system, with the installation of the ODBC driver and the creation of a simple PowerShell script using the latter.
The first step is to download and install the ODBC driver: https://pcsoft.fr/st/telec/modules-communs-28/wx28_94s.htm.
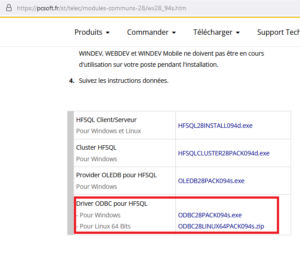
Download the executable for Windows and install it.
You can verify its correct installation with the following PowerShell command:
Get-OdbcDriver | Where-Object Name -like "HFSQL"
You can then simply interact with the driver using PowerShell. The following script allows you to test the connection to a remote HFSQL database using the default administrator account which is admin without password.
DSecBypass pentesters have made your work easier by using a built-in database, accessible by the HFSQL admin user, which allows you to execute SQL queries without necessarily knowing the name of the application databases.
The informed reader can extend this script to bruteforce authentication to the service, obviously on systems on which he has authorization.
Exploitation of HFSQL injections
SQLMap knows how to detect HFSQL injection since the language remains relatively classic SQL. On the other hand, it will not be able to exploit it because it does not detect the DBMS and does not have certain functionalities to exploit it in a generic way. This typically results in SQLMap reporting an SQL injection, discovering the exploitation method (Error, Blind, Union etc), then eventually reporting that it is a false positive.
During a penetration test, our pentester discovered an SQL injection in a WebDev application. This flaw, when it concerns HFSQL, becomes particularly sensitive: it allows an attacker to take advantage of the WLanguage language, which is an extension specific to the WinDev, WebDev and WinDev Mobile development environment.
This interconnection between WebDev, HFSQL and WLanguage offers significant potential for application development. However, it also highlights the importance of proactive vulnerability management, particularly in the context of database security. This requires constant vigilance and appropriate security measures to ensure the integrity and confidentiality of stored data.
Please note, it is not automatic that the HFSQL user has access to WLanguage functions. So your SQL injection may not be able to use this exploitation technique. However, from experience, developers frequently give these rights to the application.
Here is an example of an HFSQL query that uses a WLanguage function. To use them, simply prefix the function name with “WL.” :
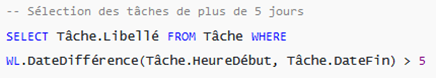
All WLanguage functions are documented at the following link: https://doc.pcsoft.fr/fr-FR/search2.awp?origin=browse&cat=wlangage,249.
Let’s go back to our SQL injection.
The auditor had manually validated the presence of the injection:
"test' or 1=1--" renvoie l'ensemble des résultats "test' or 1=2--" ne renvoie aucun résultat
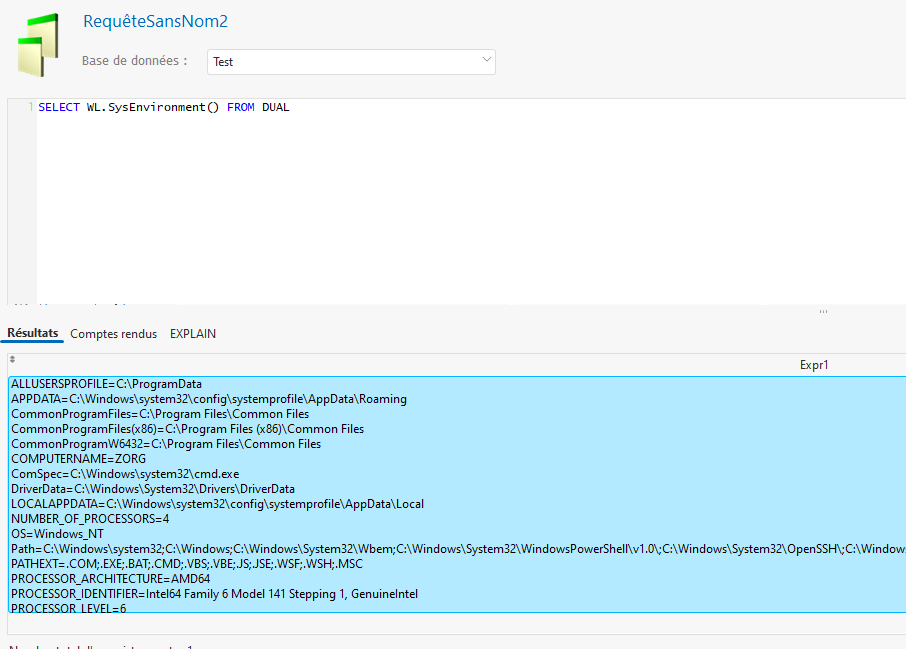
Of the “Union based” type, the injection made it possible to retrieve the result of the query which allows for example to obtain all the system environment variables using the “WL.SysEnvironment()” function:
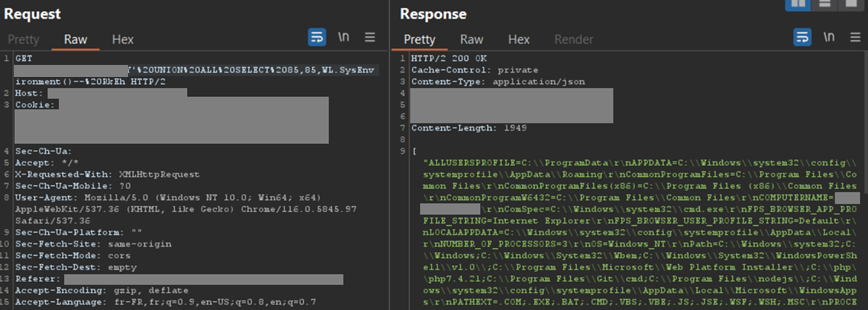
The payload is the following:
' union all select 85,85,WL.SysEnvironment()--
We can clearly see, in the application return, all the configured environment variables. Which, in certain contexts, can be very interesting.
Depending on the configurations and HFSQL version, the ExeRun (LanceAppli) or LanceAppliAssociée functions can be used to execute Windows commands on the database server. A low-level function also allows you to interact with the dlls. Note that HFSQL restricts the accessible WLanguage functions, the reader will therefore have to discover which ones can be used.
More broadly, the WLanguage functions in the “Windows management WLanguage functions” section should be tested as part of an intrusion test, in particular the Executable Functions, System Functions and Network Functions.
Replication of a WebDev + HFSQL environment locally
In order to study and better understand the security of applications developed on WinDev/WebDev it may be interesting to create a local test environment.
To do this, you just need a Windows virtual machine and install the WebDev environment (including HFSQL and IIS which will be offered to you during installation). The VM prerequisites are available at the following link: https://doc.pcsoft.fr/?2036002.
To test the execution of WLanguage functions from HFSQL, once all the components have been installed, add a new user using the WebDev Hosting Control Center by granting him all rights to the database, in particular the “Right to execute stored procedures”.
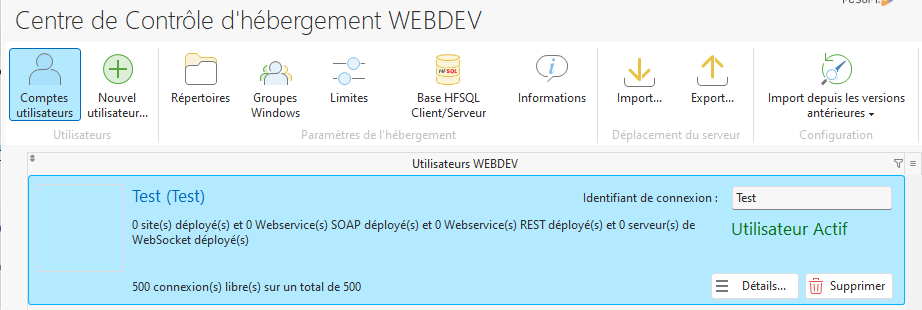
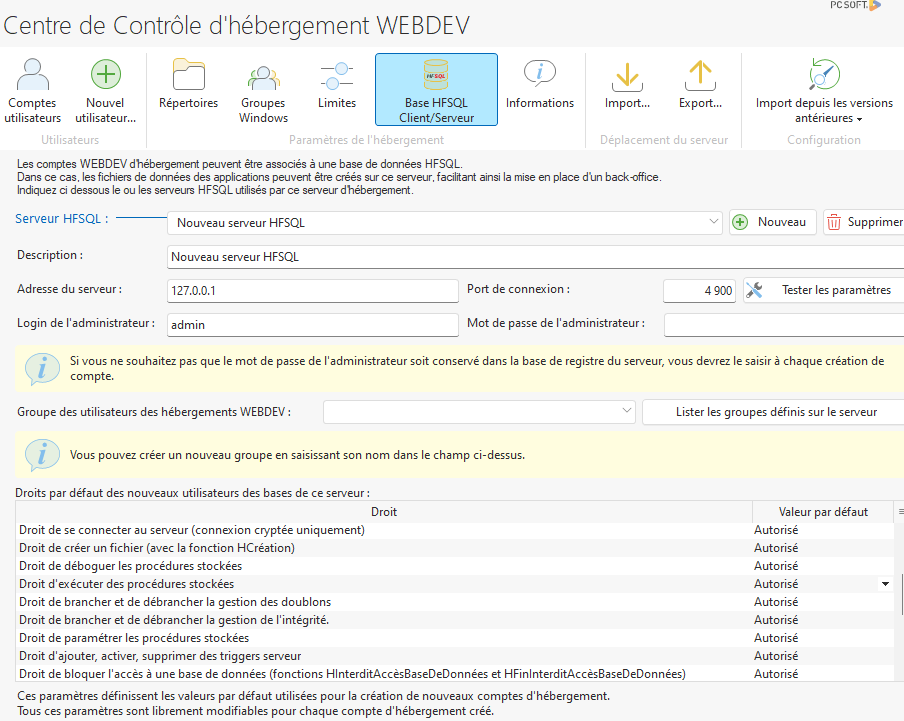
Then check that you can execute the WL functions using the HFSQL client configured with the user thus created:
Numerous possibilities for research into the security of the WinDev/WebDev environment exist: analyzing communications between the HFSQL client and the server, analyzing the security of WLanguage functions (fuzzing of parameters for example), studying the possibilities of privilege escalation locally, and many others.
What about the recommendations?
In order to deploy WebDev applications with HFSQL in the best security conditions, the following advices can be considered:
- Implement PC SOFT security recommendations: https://doc.pcsoft.fr/fr-FR/?1000017310
- Make sure you have a complex password for the HFSQL Admin account
- Use system users who have restricted rights
- Grant only the strictly necessary rights to the HFSQL user
- Expose HFSQL network services only to hosts and networks that need access to them
- Use parameterized HFSQL queries when you need to build a query from data that comes from the frontend
- Use the WLanguage HTMLVersTexte() function to protect against XSS
- Train your developers in secure development best practices
🛡️ DSecBypass supports you in the security audit of your web applications as well as in training developers in good security practices. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
