
Vladimir had the opportunity to test the security of KeyShot 11.1 software during a penetration testing mission.
This software, published by Luxion, is used to produce photorealistic 3D renderings in real time. It requires significant computing capacities which can be distributed on several servers thanks to KeyShot Network Rendering.
In the case of a distributed architecture, one or more managers must be configured to manage user accounts and distribute tasks to different workers. The end users of the software then use their local client to authenticate with the managerand send him the tasks to be distributed.
The KeyShot Network Monitoring thick client (“keyshot_network_monitor.exe”) allows users to authenticate and access the progress status of tasks and the occupation rate of workers.
Network protocol analysis
Clients communicate with the manager on port TCP/4827 using a proprietary protocol. Communications are in the clear by default but TLS encryption can be configured. During the audit in question, encryption was not enabled.
The DSecBypass auditor decided to analyze the unauthenticated attack surface exposed by the manager. To do this, he used KeyShot Network Monitoring with a valid account to reverse-engineer the communications between the client and the manager.
Wireshark software was used to capture the different packets exchanged. The consultant interacted with the software, taking care to use the most important features so as to generate maximum traffic and be able to identify which sequences of bytes govern the actions.
In order to isolate the packets of interest in the conversation, simply create a filter on the manager’s IP address as follows:
ip.addr == 192.168.1.1
Then decode TCP stream from filtered packets:
A window opens and displays the characters that can be displayed, colored according to whether they are sent or received.
This window is useful for following the progress of the conversation between the client and the manager. When an interesting message is discovered, simply click on it to highlight the corresponding packet in the Wireshark capture window.
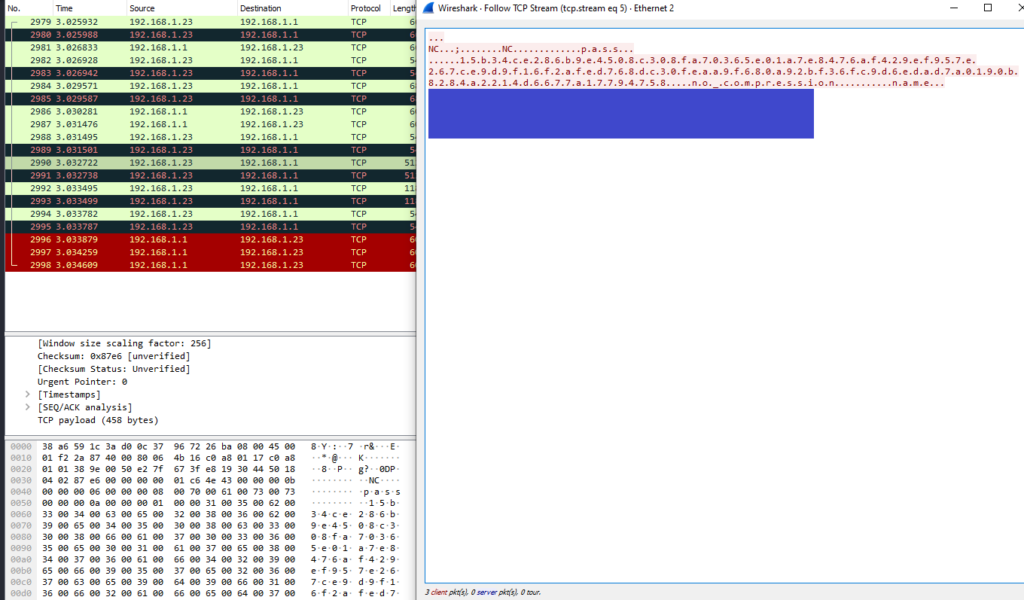
The screenshot above shows the package selected by clicking on the “pass” string of letters.
In order to extract the message as it is, all you have to do is export the TCP data (data or payload TCP):
The auditor was thus able to export the messages corresponding to the authentication, the recovery of information on the tasks in progress, the change of information of a user and other interesting actions.
An important part of the analysis was to understand how the packets were formed and in what order they were sent to the manager. It is also important to analyze the manager’s responses, in the same way, in order to know if the previous message was rejected or not.
Packet replay and forging
Once the different messages have been isolated, it may be interesting to replay and modify them.
The auditor relied on the Python pwntools library: CTF oriented, it is optimized for pwn/reverse type challenges and allows in a few lines to interact with TCP sockets.
A few bash commands are also useful:
#Inspect message bytes
xxd fichier.bin
#Compare octets between two files and display offsets
cmp -l fichier1.bin fichier2.bin | gawk '{printf "%08X %02X %02X\n", $1, strtonum(0$2), strtonum(0$3)}'
#Replace a series of bytes with another in a file (useful for modifying a string for example)
xxd -p -c 123456789 fichier.bin |sed 's/0011002200330044/0011003300220044/g' | xxd -p -r > fichier2.bin
Identifying the bytes specifying the size of the message and the various fields is left as an exercise for the readers.
The following Python script template can be used to easily send the prepared messages to the manager:
The vulnerability
Using the methodologies described in the previous paragraphs, the auditor managed to find a security flaw in the protocol in one day of analysis. The final POC will not be disclosed.
The vulnerability, discovered by Vladimir, allows an unauthenticated attacker with access to port 4827 of the manager to bypass authentication in order to obtain the list of users created, then in the same way request information concerning them (date of last update, email address and role).
This information leak could allow an attacker to attempt a brute force attack on discovered accounts or social engineering using email addresses.
Not having a direct impact on the security of the distributed infrastructure (non-privileged and non-admin actions), this vulnerability presents a risk qualified as important with a CVSS score of 5.3.
Communication with the software publisher
Communication with the publisher Luxion went remarkably well: the vulnerability disclosure process is well documented at https://www.keyshot.com/csirt/, the security team responded within the day, and the vulnerability was validated and fixed in the following days.
KeyShot 11.2 release fixes this vulnerability.
Luxion documented this new vulnerability in their LSA-989246 and credited Vladimir TOUTAIN of DSecBypass for discovering this vulnerability in KeyShot software.
21/06/2022 : First mail sent to [email protected]
21/06/2022 : Response from Luxion and details sent by Vladimir
27/06/2022 : Mail from Luxion indicating that the vulnerability has been validated and fixed since 21/06, sending a beta version with the patch
27/06/2022 : Luxion sends a first version of advisory LSA-989246 for validation, agreement on a deadline of one week after the publication of version 11.2 to communicate on the DSecBypass side
29/06/2022 : Version 11.2 released with the vulnerability fix
06/07/2022 : Validation of this blog post by Luxion
🛡️ DSecBypass accompanies you on the security audit of your applications. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
