DeepReview (https://deepreview.app/) is a project created by students from INSA and EFREI: it’s a CTF-type platform for discovering or deepening code auditing, with an approach based on real vulnerabilities (CVEs) rather than theoretical exercises. It is ideally suited to beginners who need guidance in understanding potentially complex CVEs without having the necessary knowledge of cybersecurity or a particular language.
The project being a fine initiative, and DSecBypass being particularly attached to this CTF / self-taught universe, we decided to take a look at it with three objectives: flagging, acquiring new knowledge, contributing if possible to this project by checking its safety.
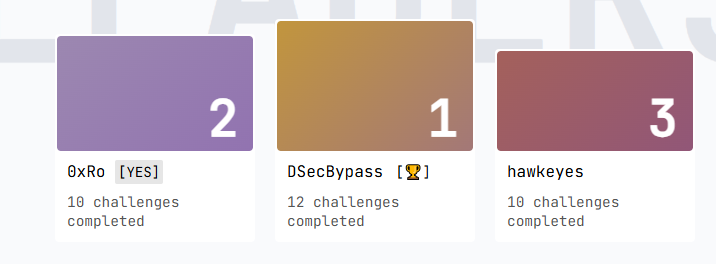
First by far
At the time we started the challenges, there were 10 exercises open to everyone and 1 accessible to sponsor profiles. That’s 11 exercises.
In the form of quizzes, the exercises are fairly simple and quick to complete, so we quickly achieved a 10/11 pass rate, as did several other players at the time.
A closer look at the exercises available on the platform at the time reveals that the creators used an existing Github repository to launch their project with a minimum of content. The sponsor challenge, on the other hand, was an original creation, but with restricted access. The repository is
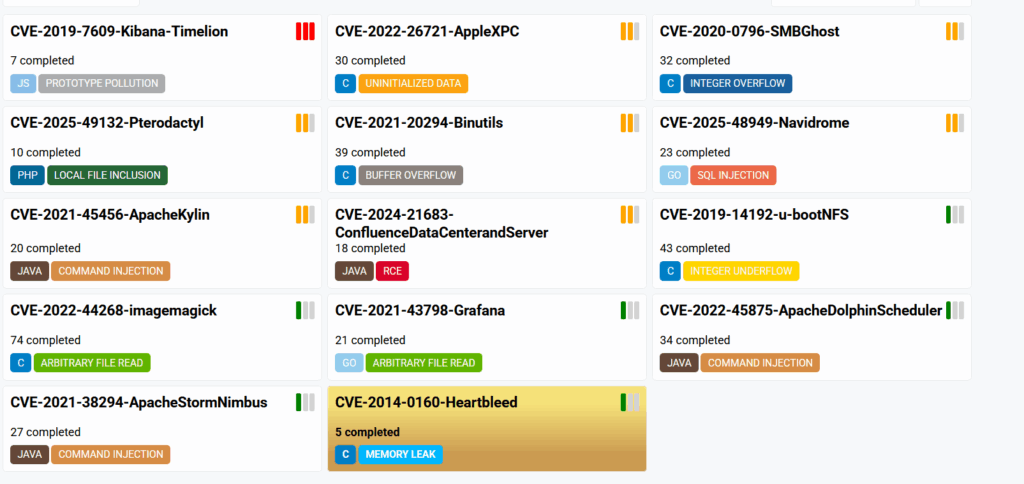
The web platform hosts these exercises and sends the answers to the server, which checks them and validates the challenge once they are all correct.
Answer validation involves a POST request with the answer number (an integer that increments in the URL) and the expected answer (a line number, a function name, etc.). For example, here we send “funcName” as the answer to question number 89.
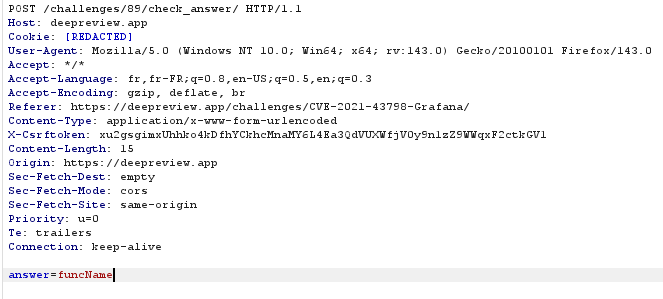 Another important point is that answer numbers follow each other within the same challenge: if the challenge has three answers and the first one is a POST to “/challenges/89/check_answer/”, then the next two will be 90 and 91.
Another important point is that answer numbers follow each other within the same challenge: if the challenge has three answers and the first one is a POST to “/challenges/89/check_answer/”, then the next two will be 90 and 91.
If we put ourselves in the creators’ shoes, we can imagine that it would be interesting to import all the exercises from the repository at once, then expose only a few selected challenges and unlock them easily as we go along. It is therefore conceivable that the answers to exercises not yet displayed on the DeepReview frontend have been integrated into the backend. If access control is poorly implemented, we’ll be in a classic IDOR vulnerability, allowing us to validate challenges that nobody else can validate (unless they have the same idea as us).
To test our theory, we simply took a challenge from the repository that hadn’t yet been exposed on the platform, chose an answer that’s unlikely to have been modified (code line numbers may vary between the platform and the Github repository), then bruteforced the answer ID until it’s valid. This way we would know that the adjoining responses would validate the “Ghost” challenge. This is what we’ve done with Burp Intruder:
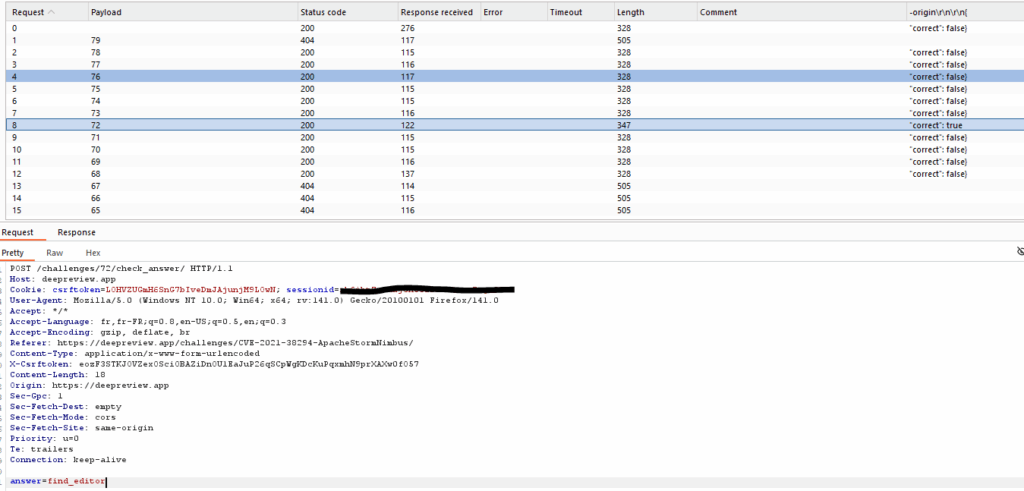 In this screenshot we see Burp’s Intruder feature iterating over the response number, sending “find_editor” each time until a valid response is found (grep-extract “Correct”: “true” in the server response). Here, response number 72 corresponded to this exercise.
In this screenshot we see Burp’s Intruder feature iterating over the response number, sending “find_editor” each time until a valid response is found (grep-extract “Correct”: “true” in the server response). Here, response number 72 corresponded to this exercise.
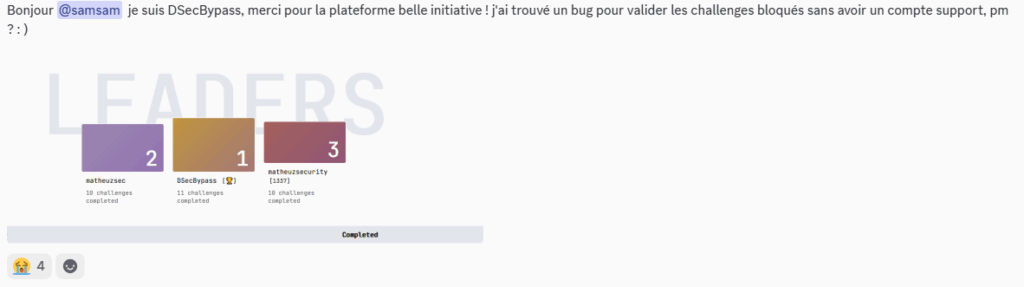
By validating the other answers in the ghost exercise, we managed to flag up the challenge even though it wasn’t proposed, and reached 11/11 completion without even having done the sponsor challenge!
Of course, we immediately notified the platform’s creators via their Discord :
 The bug was quickly fixed. We had recommended correcting the permission flaw AND switching to UUIDv4 to reference responses so as not to be able to enumerate them in the event of another IDOR being exploitable, but UUIDs has not yet been implemented at the time of writing. The “sponsor” status has been kindly granted to us to thank us for helping to secure DeepReview :
The bug was quickly fixed. We had recommended correcting the permission flaw AND switching to UUIDv4 to reference responses so as not to be able to enumerate them in the event of another IDOR being exploitable, but UUIDs has not yet been implemented at the time of writing. The “sponsor” status has been kindly granted to us to thank us for helping to secure DeepReview :
![]()
We were therefore quick to flag the sponsor exercise, an original creation by DeepReview, thus increasing our completion rate to 12/10.
It’s a great project: don’t hesitate to come and discover the existing exercises and contribute by proposing new challenges on their Discord!
🛡️ DSecBypass can help you audit the security of your APIs and web applications. Do not hesitate to contact us for additional information and/or a personalized quote 📝.
